Product Update - v21.47
Features
Announcement: New design for Flows page
We would like to inform you all about the impending roll-out of the new Flows page during our next 21.49 release (9th of December 2021). Our OEM customers will receive the detailed explanation of changes in advance.
The platform user interface has gone through changes in the last year. Some pages like the Executions and Logs use the new unified design. We have still some way to go for a complete transition into the new unified look.
Our team has been working hard to transition the Flows page as well. We are ready to show you what is coming during our next release in two weeks:
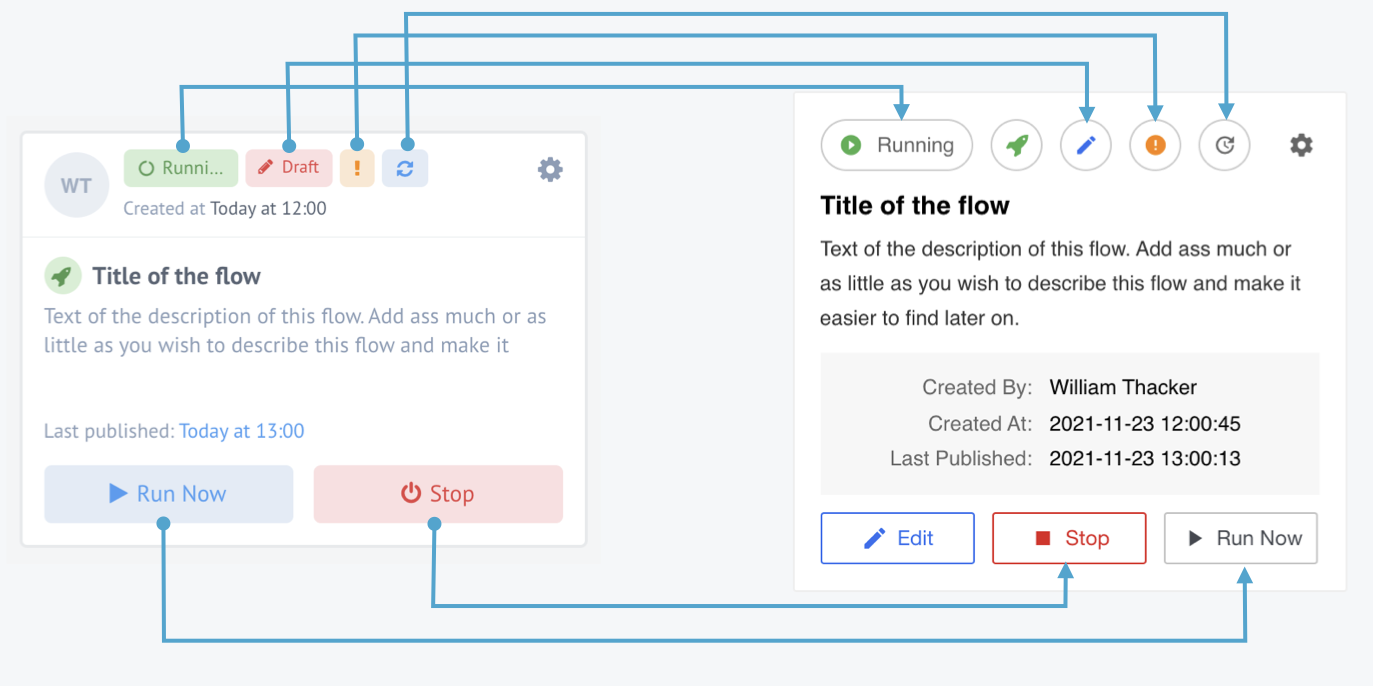
Picture shows the flow card changes.
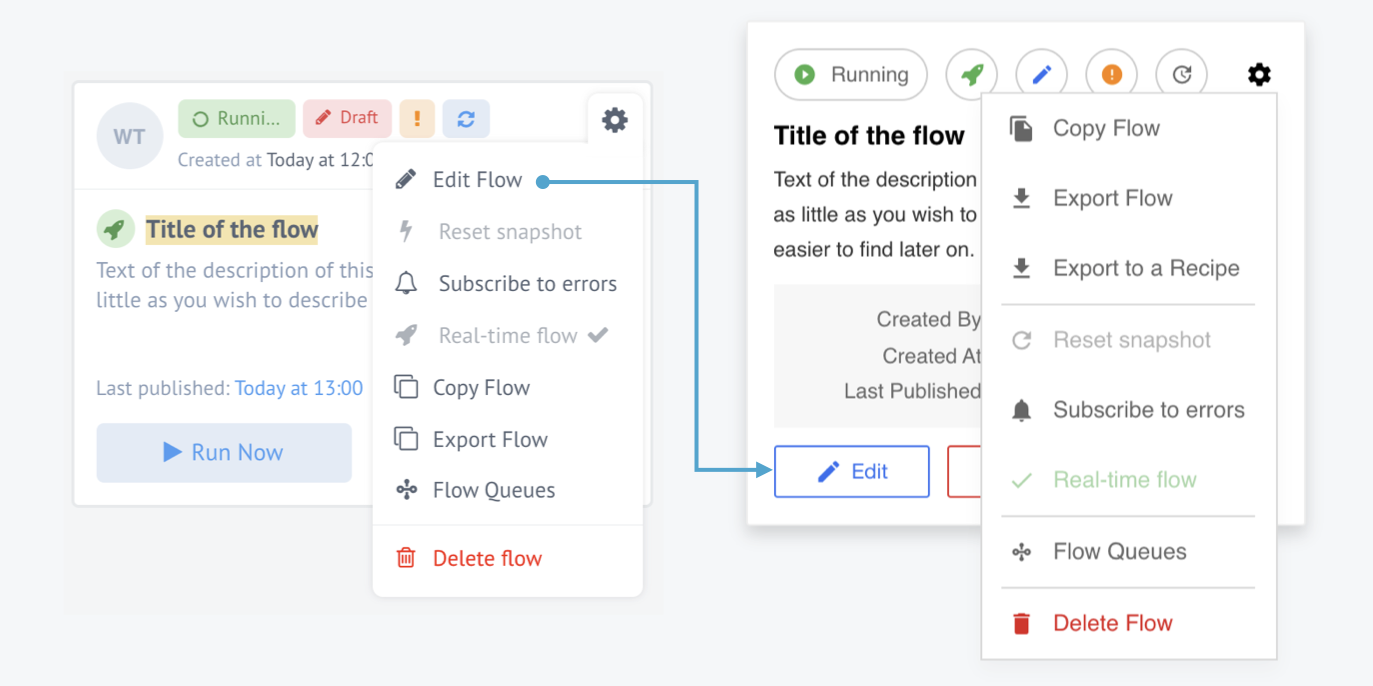
Picture shows the flow card menu changes.
Improvements and Updates
The release 21.47 release contains behind the scene improvements to the platform backend, more relevant to our OEM and on-prem customers.
- Introducing support for Elasticsearch API version 7.
- Adding
SCRAM-SHA-256authentication for MongoDB. - Commons: update mongoose to
5.13.13version. - API: update mongoose to
5.13.13version.
HELM3
We constantly improve different aspects of HELM3 deployments in collaborations with our partners. This section lists updates and improvements done in this round.
Quota service health-check problem
During the 21.45 deployment of flow quota feature the sync process was failing the health-check and the Kubernetes was constantly killing it. Our investigation showed that the sync process must be done in batches. For this purpose we introduce the following new parameters.
Api:
SyncMaster QUOTA_SYNC_BATCH_SIZE is equals 20 by default
Quota service:
Added MAX_BATCH_SIZE environment variable (50 by default)
Helm:
Values.secrets.platform.config.QUOTA_MAX_BATCH_SIZE- Optional. Use to override default value of maximum batch size limit in the/resources/{resource}/applyendpoint.Values.secrets.platform.config.API_QUOTA_SYNC_BATCH_SIZE- Optional. Use to override default value of batch size for the Quota synchronisation.
OEM Related
News in this section are for our customers who use OEM version of the elastic.io platform.
Custom login and logout redirects
With 21.47 we introduce a possibility to configure custom login and
logout redirect URL for our OEM customers. You can use this with OIDC or SAML
providers to streamline and unify customer management in your entire ecosystem.
To setup redirects you need to update (PATCH) your tenant record and add the required
parameters following this example:
"login_redirect_sso_provider":{
"type": "openid",
"id": ""
},
"logout_redirect_url": "https://sso.example.com/logout"
Our API documentation contains the instruction on how to update tenant record.
Along with this addition we introduce a new API endpoint for deleting the OIDC provider record: DELETE /v2/tenants/{TENANT_ID}/openid/providers/{OPEN_ID_PROVIDER_ID}
Fixed Bugs
- Fixed the mapping user interface bug when the first character of a dot in the value in the array fields would disappear.
Components
Hubspot Component 1.3.0
- ADDED Create Association action
- ADDED Delete Association action
- ADDED Lookup Set Of Objects By Unique Criteria action
- ADDED Lookup Objects action
- ADDED Delete Objects action
- ADDED Webhook trigger
ZOHO CRM Component 1.2.0
- ADDED Lookup Objects action
- ADDED Delete Object action
Rest API OAuth2 Client Credentials Component 1.0.0
- ADDED HTTP request action