Product Update - v22.20
Improvements and Updates
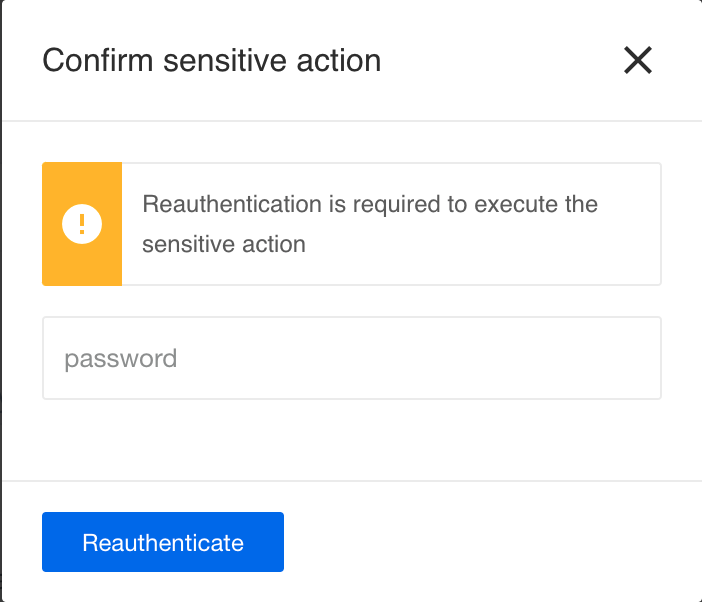
Re-authentication for sensitive actions
While working on the platform interface it is possible that users can accidentally change or delete important or sensitive information.
For such cases we introduce re-authentication for sensitive actions. After 22.20 for the following actions you will be asked to enter your password to authenticate:
- Reading, copying and regenerating your API Keys.
- Modifying your user details.
- Disabling 2-Factor Authentication (2FA).
- Inviting members to contracts.
- Inviting and removing members from workspaces.
Please Note: You will be asked to re-authenticate once every 6 hours.
Email verification during registration
To prevent erroneous and bot registrations we introduce email verification step to our trial registration process. When you register first time with our platform, an email will be sent to your given email address. Click on the link in your received email to finish your registration. There are certain rules and restrictions to this process as well:
- If you register using Single-Sign-on (SSO) Provider (OIDC/SAML) then the platform will not ask to verify your email address since you have verified it with your provider.
- You must wait for 30 minutes before you can use the same email address to register.
- The invitation to confirm your email is valid only for 1 day.
Please Note: If you are invited to the platform directly, no email verification will be required.
HELM3
We constantly improve different aspects of HELM3 deployments in collaboration with our partners. This section lists updates and improvements included in this release.
Separate MongoDB for Maester
When your integration flow needs to transfer big objects or attachments, one of the platform microservices called Maester temporarily stores them in MongoDB while passing only the object IDs through the integration flow steps.
Starting from 22.20, you can use a dedicated database for storing Maester
objects and the run-time attachments. To configure, add MAESTER_MONGO_URI
environment variable to HELM3 secrets charts and set it to target this new database.
Note: You will need to migrate the grids to new MongoDB as well to ensure the Maester object availability after implementation.
Organisations who do not need a separate MongoDB instance to store their Maester
objects should set the MAESTER_MONGO_URI variable to the same value as the
MONGO_URI variable. This will save objects in your main database.
Setting authentication token lifetime
To configure the re-authentication for sensitive actions:
- Add the
SENSITIVE_ACTION_AUTH_LIFETIMEenvironment variable to HELM3 secrets chart and set it to specify how long user authentications are valid. The system expect the value of this parameter in milliseconds. The default is set to 21600000 (6 hours). - Enable the
tenant.featureFlags.sensitiveActionsReauthfeature flag (set it totrue).
OEM Related
Information in this section is intended for our customers who use OEM version of the elastic.io platform.
White-labeled credential management
Developing integrations requires a certain level of access to business systems. In cases where the integrators are not responsible for these systems it is critical that only secure access is allowed and that system admins can control credentials used To solve the dilemma we introduce White-labeled credential management feature.
How does the White-labeled credential management work?
As an integrator you provide a unique URL to the credential holder to enter their access credentials without registering or logging-in to the system. The access holder is presented an interface to enter their credentials, verify them and save.
In addition they can modify the existing credentials as well.
For both cases they are presented with a simple screen to work with only the specified credentials.
How to generate unique URL?
There are certain preconditions before you can enable this feature:
- The end customer is already in the DB. This means you have to create a user for your credential holder, then add him/her to the contract and workspace where the integration is to be developed. All these actions you can do with API calls using administrative access.
- The newly created user must have only access to the credentials entity.
- Your tenant has SSO provider (OIDC/SAML) with
autoCreateUsersset tofalse.
Once the above conditions are met you can take the following steps to generate the URL to request credentials from their owner:
The initial URL has a form /embedded-credentials/repoId where the repoId
would be the ID of component for which you need to set the credential. Then you
would need to add the following query parameters to this URL:
workspaceId(required) - this is the ID of the workspace where integration is set.ssoProviderType(optional) - values can beSAMLProviderorOIDCProvider.ssoProviderId(optional) - this is the ID of your SSO provider.
Let us construct the URL:
TENANT_URL/embedded-credentials/[repoId]?workspaceId=[workspaceId]&ssoProviderType=[ssoProviderType]&ssoProviderId=[ssoProviderId]
If you do not specify ssoProviderType and ssoProviderId then they will be
automatically taken from the tenant.loginRedirectSsoProvider property but only if this is defined.
Setup Email verification
To set the email verification process
in your tenant the following must be done using an API call to update your tenant records using tenantAdmin privileges:
- Enable the registration page - set the
attributes.hide_registerparameter tofalse. - Use
signin_v_2type - add theattributes.signin_v_2attribute containing the URL of the provider logo using theattributes.signin_v_2.logo_urltenant parameter. - Enable
email_verificationfeature flag (NEW) - setattributes.feature_flags.email_verificationtotrue.
Fixed bugs
- Fixed the error
Cannot add property token, object is not extensibleappears in the platform user interface when trying to evaluate JSONata expressions with"$count()".
Components
PayPal Component 1.3.0
- ADDED
Receive Instant Payment Notificationtrigger - ADDED
Receive Payment Data Transfertrigger - ADDED
Webhooktrigger - ADDED
Create Objectaction - ADDED
Update Objectaction - IMPROVED input metadata in the
Make a Paymentaction
Microsoft One Drive Component 1.0.5
- UPDATED the
component-commons-libraryto read and upload attachments through theMaester - UPDATED Sailor version to
2.6.27 - UPDATED dependencies and addressed the packaged vulnerabilities
Shopify Admin Component 1.6.0
- ADDED validation
HMACsignature for theWebhook subscriptiontrigger
Petstore Component Java 1.0.6
- IMPROVED the security by adding an automated vulnerability check run in CI/CD
JDBC Component 2.5.4
- IMPROVED the security by adding an automated vulnerability check run in CI/CD
Vtex Component 1.4.1
- ADDED
Place Orderaction - UPDATED dependencies and addressed the packaged vulnerabilities
- ADDED the component pusher job to
Circle.ciconfiguration.
CSV Component v3 3.1.4
- FIXED memory leak on
Emit Batchbehavior for theRead CSV attachmentaction
Updates to multiple components
As a part of our on-going improvements of integration components, we
- UPDATED Sailor version to
2.6.27 - UPDATED dependencies and addressed the packaged vulnerabilities
- ADDED the component pusher job to
Circle.ciconfiguration.
Here is the list of components for 22.20 release.
- Marketo component
2.2.4 - AWS S3 Component
1.4.3 - HJSON Component
1.0.1 - Zoho CRM Component
1.3.2 - Git Protocol Component
1.1.3 - Google Spreadsheets
2.0.2 - Salesforce Component v1
1.3.9 - Salesforce Component v2
2.2.2and2.2.3 - Simple Trigger Component
1.1.6 - Delta Detection Component
2.0.3 - Utility Component
1.4.1 - Magento2 Component
1.6.6 - GraphQL Component
1.1.2 - Pub-Sub Component
1.0.8 - MongoDB Component
1.5.9 - CSV Component Old
2.2.1 - Dictionary Component
1.1.6a.k.a Lookup Table Component - ZIP Component
1.1.5 - XML Component
1.3.5 - Meracdo Pago Component
1.0.1